
- ProPakistani faced hacking attempt
- ProPakistani remained down due to a WordPress Bug
- Attacker was traced by ProPakistani team
- Mr.c0d3r, who allegedly launched DOS on ProPakistani is Lahore based
- He is allegedly involved in defacing Rehman Malik’s website, FIA, Geo NEWS and various other websites
- Its Pakistan’s first case study on hackers that has been traced with all the forensic procedures being followed, systematically.
Details
As you may know, on January 18th, 2009 at 11:15 PM, ProPakistani website stopped responding web requests. Most of the visitors were given a 500 html error – also database connection error.
We were able to bring back a optimized form of ProPakistani pretty soon, however ProPakistani server remained critical for next 48 hours – During which, we remained down for some time for maintenance.
We thank our visitors, who remained intact with us during all this and showed their tremendous concern though emails, phone calls, Facebook queries and so on.
We had promised our readers that we will public everything regarding the down time, cause for the problem and other relating information.
ProPakistani faced Hacking Attempt
The news is that ProPakistani had an unsuccessful hacking attempt, and attacker remained un-successful in defacing ProPakistani. However, he managed to do a DOS attack.
Good News: We Have traced the Hacker
Good News is that we have tracked the attacker, with all the proofs. Its first time in history of Pakistan that a hacker had been traced with all the forensic procedures being followed, systematically.
Security Operations were lead by renowned Muhammad Ali Raza. We thank Sohaib Ather for his extra ordinary services for Database and Server Optimization during this.
Below are complete details for your information only.
What had happened?
Immediately, after the attack was launched at 11:15, we thought it was a usual SQL server crash; however, server reboot and Dabatase repair and optimization didn’t work and crashed again very soon.
Database tables kept crashing, despite re-boots and repairs, even backup got crashed when restored. With-in first 30 minutes we had known that this is not software or database glitch, and it was some external attack.
ProPakistani servers are DDoS proof, so there were little chances that someone was launching a DDoS attack. After diagnosis, we were able to determine that was a DOS attack, instead of DDoS attack.
It happened due to a WordPress Bug!
We identified that WordPress version 2.9.1 is vulnerable from DOS attack. Bug lays in its coding that uses cache stressing with random parameter on multiple requests. WordPress has been notified about the issue; however, bug is still pending resolution. But we have secured ourselves, thanks to alternate technologies.
How Attacker Impacted?
The web requests (from attacker) were not coming from multiple hosts rather it were coming from a single host with random parameter on multiple web requests (dozens of them per second). These requests were of bad or long SQL requests, ending up with a database crash.
As the bug was in its core of WordPress so we couldn’t pull WordPress down. We had to come up with different solution. We tried moving the entire server to a new place, did tons of Database optimization, server optimization and all other options that we could avail.
While Shoaib Ather and his team were busy with database and server optimization, Ali Raza remained busy with tracing the route of attacker. He was able to trace back to the attacker successfully. However, information that we got was pretty shocking for us.
On 20th January, 2009 ProPakistani was working back with normal broadcast.
Who was Attacker?
Note: We didn’t penetrate into any personal computer/system, and used all publically available information for tracking.
We only had source IP at that time (through our Apache Error Logs).
Source IPs of attacker included:
- 66.96.219.37
- 64.22.101.106
- 66.219.58.34
When sought, these IPs were registered in the name of an American ISP. When inquired, ISP was kind enough to give us the name of company who had been allotted these IPs.
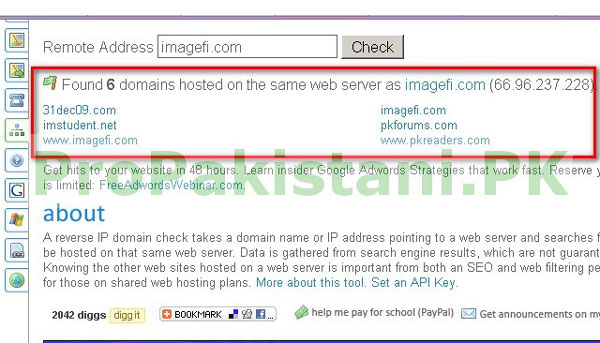
As per American ISP, these IPs were registered in the name of a company called, ImageFi (www.imagefi.com). While IPs were mapped against the same VPS that hosted www.imagefi.com
American ISP also confirmed us traffic routing from above mentioned IPs to ProPakistani.PK – they assured us they will provide us logs, if asked.
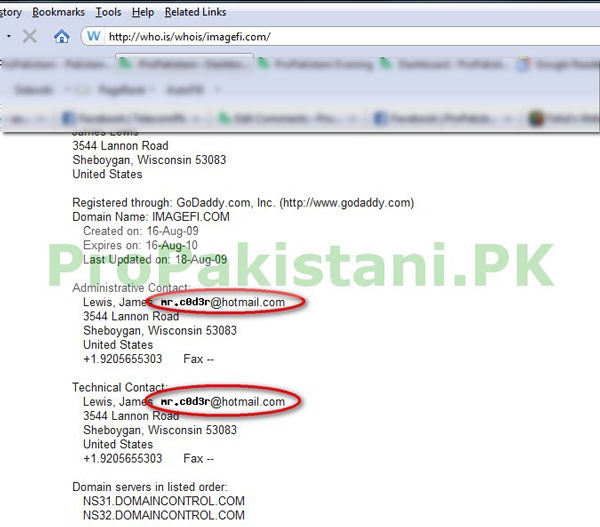
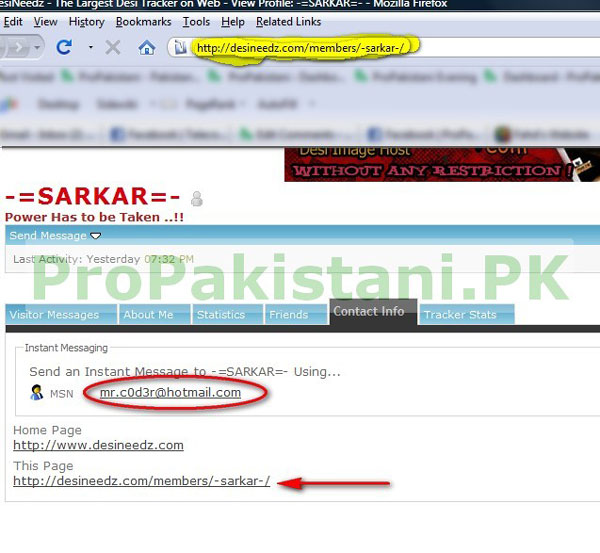
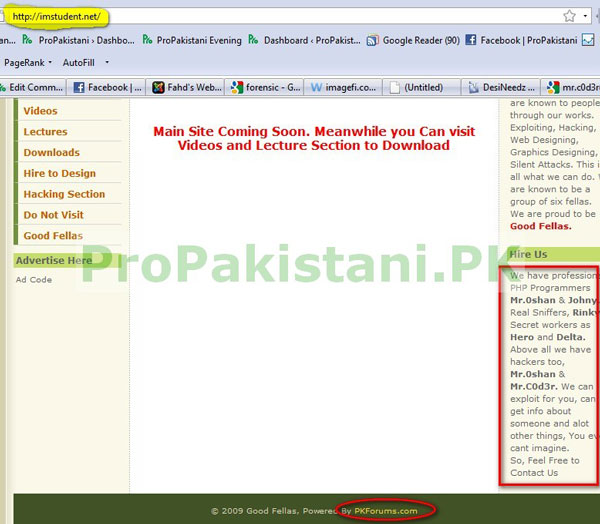
WHOIS of www.imagefi.com revealed that [email protected] had the ownership of one of those domains.
It was further shocking for us when we found out other websites that are hosted on same VPS, check below screen shot for proof…!
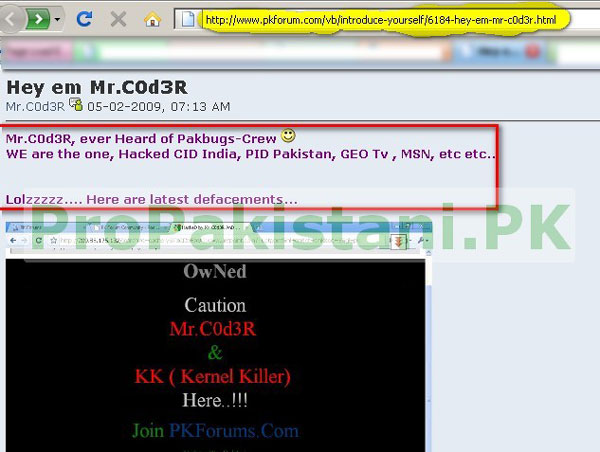
When searched on Google, Mr.c0d3r was found as a crew member of pakbugs.com. However, reportedly, he is no more associated with Pakbugs.
Digging further into Google, we disproved more interesting facts about this mr.c0d3r. He is running a torrent portal and trace leads us to India.
Googling this email [email protected] revealed tons of other information and soon we were able to find out that this guy is not from India.
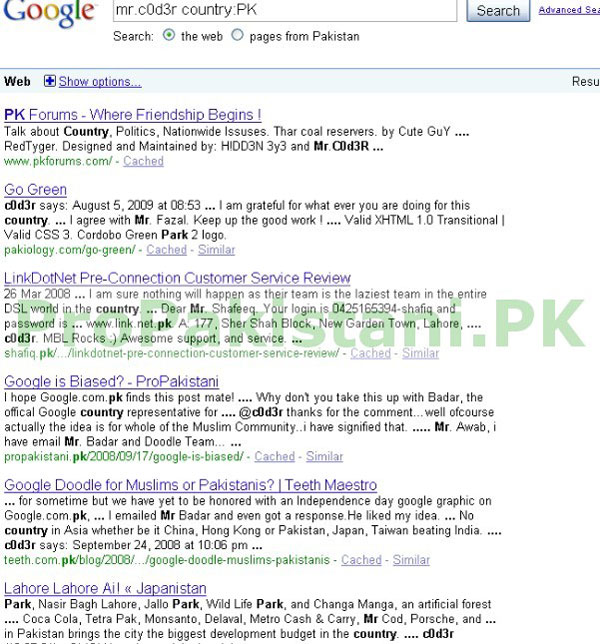
When you Google with this particular query “mr.c0d3r country:PK” its shows that he has involvement with a local blog and forum.
So this mr.c0d3r is the guy who owns PKforums and PkReaders.com
We already have notified NR3C, with all the proofs and details to do the prosecution.
We do have all server logs saved. We do have phone numbers and address details of this person too. Will be given to concerned authorities during investigation.
This case study has been prepared by ProPakistani team.
Special thanks to Fahad Aziz and Sohail Abid for their support





















very well done ProPakistani team … good job.
Aala report. Impressed.
Terrific work there, Aamir. Pkforum guy behind this? Shameful indeed!
its pkforums.com
pkforum is owned by someone else…!
I dont Understand the Purpose of Hacker…they can just Irretate the People who Entertain multi people & give Strong Information…..what have Hacker Problem with that….
they can do this work just for Fun!!!
Shame Hackers People…..
Well Done Propakistan Team
yes the purpose of this kinds of activity is only fame to them nothing more but sometimes they do take it personally and in here i think this is the case.
Aa well mr Rizwan no one did any thing wd 0ut purpose actually taking down any server or Blog indicate hacker want something special that rank in ur blog or server .. I am against Ddos because I am a victim. .
AAAAllllaaaa!!!
Nice
Good investigation! :)
Its no secret WordPress comes wit a lot of security vulnerabilities.
Seems the hacker uses same names everywhere and this is why its so easy to find his contact details.
What Pakistani authorities one should contact in such scenario?
Its the FIA cyber crime wing that you contact with proofs and written application.
WordPress is indeed a open source project but this doesn’t mean that its not secure. The reason of using it because its flexible to our need.
it wasn’t easy at all. 1st trace lead us to India then i thought that they are two person sharing same name but after hours passed things started to get interested.
Awesome Propakistani team! hats off…seems like these so -called code junkies just want to show off and nuffin else…hope cyber crime div takes good care of them.
Good that you have shared the investigation report. It will keep others away from getting into such practices.
Welldone! Excellent work.
We come to know a loophole in WordPress 2.9.1.
The positive thing was that if he tells about the loophole to WordPress team rather than he utilizes the WordPress weakness.
Be Positive.
This case study has been done by ProPakistani team and we are “prude” to have such minds with us. what does it mean?
By the way it’s really fantastic
What a moron script kiddie, to attack a website of his own nation.
The saying “Allah Ganjey Ko naakhun ne de” fits right on such kinda of n00b wanna-be hackers.
Apparently you are too proud and misspelled proud :)
lol – my bad, removed the line : – )
Gud Job ProPakistani.
So India is involved here too?
And, this bloody piece of shit has roots in India?
..
We need to be notified when that swine is behind bars and reveal how he has roots in India.
..
Best wishes for ProPakistani and its team.
Fantastic guys!!
Will this guy be be charged for the cyber crime? Are there any cyber crime laws in Pakistan?
yes – already reported the concerned
You should move your website to another platform as wordpress is open source and its code is easily available giving hackers the ability to find bugs in it and then launch attack on it.
Open Source software is the second meaning of ‘secure’ software. Security issues found are fixed very fast, besides, you let the whole world find issues in your software, that way most overlooked issues are pointed out one way or another and are instantly fixed.
Compare that to closed source software where the team has to find itself issues with software and they can’t find all issues in their software which lead to some hacker finding an issue and then breaching security by taking advantage of that knowledge.
totally agree with you milkywayer
good work done by pro team
Very well done!! Hats off to you guys!!
Live long Pro Pakistani!!
He is just immature he use only one id and ip so he get caught or traced otherwise if he use Zombies it is impossible to trace him … i am not saying what he did is right, just commenting :)
Great job Ali Raza and Shoaib Ather….!
Kia baaat hai…impressed
Asalam U Alaikum
Great Job Aamir Brother
Thats Awesome .. Keep it up
wah wah wah !!
Aamir bhai maza agaya yaar sa*ay ko chhorna nahi.
very very well done..
great job
Dear ProPakistani Team, these attacks were not from us. Please double check, your this statement is totally wrong!!
“While IPs were mapped against the same VPS that hosted http://www.imagefi.com”
Please check that:
— PING imagefi.com (66.96.237.228) 56(84) bytes of data. —
64 bytes from 66-96-237-228.hostnoc.net (66.96.237.228): icmp_seq=1 ttl=55 time=115 ms
64 bytes from 66-96-237-228.hostnoc.net (66.96.237.228): icmp_seq=2 ttl=55 time=120 ms
64 bytes from 66-96-237-228.hostnoc.net (66.96.237.228): icmp_seq=3 ttl=55 time=120 ms
64 bytes from 66-96-237-228.hostnoc.net (66.96.237.228): icmp_seq=4 ttl=55 time=120 ms
ImageFi.com is my domain and it is hosted with IP 66.96.237.228 and none of these mentioned IPs include my sites.
And yes all these sites are mine, as you mentioned above, and most of them are on same IP as for imagefi.
And regarding the reported IPs, anyone can buy a server/vps hosting by simply putting domain name as “www.imagefi.com” and host name with same or whatsoever he wants.
Like one can also buy a server with host name and domain name as google.com or propakistani.pk but that does not mean that google or propakistani are actually being hosted on that server.
For that you need to park your domains there, but you can see none of my domains are there.
So how anybody can claim this that it was from us?
We have nothing to do with ProPakistani, and we heartily respect the team propakistani, as i myself am a permanent reader of ProPakistani and i ahve no intentions to do all this.
BTW, such a lame investigation has been projected as an extremely professional one. Lolz at these guys who say they are security experts. Knoing buzz word and googling doesn’t make you professionals.
impressive work done! good job guys
Hi,
Thanks for your detail information.
Same case i was caught in 2009 when our client website was hacked and when i detail worked, check logs everything and then contact to that ISP when the Culprit used and we catch the detail logs from ISP and finally the person was in Defence Area Karachi.
Then what? what you then after locating him ?
did*
admin/amir: I could not find any connection b/w 66.96.237.228 (imageFi.com) and the three IPs you claim to be the attackers source. Searching http://ws.arin.net/whois/ for those IPs shows that they belows to three different ISP. So I do not understand how did you link them to imagefi?
We have put forward what we had collected, charging someone, and doing the investigation is not our part. We have a govt authority for that matter
yes exactly…. but statements like
– Mr.c0d3r, who allegedly launched DOS on ProPakistani is Lahore based
– Good News is that we have tracked the attacker, with all the proofs.
mean you really think c0d3r is really behind it and for that you really have some solid proofs which you have not shared with us. Because the proof you mentioned above do not prove any relationship b/w imagefi and the three attacker IPs.
Anyway, I hope that you will keep us updated about any new development. Best of luck.
bro, allegation by definition is: An allegation (also called adduction) is a claim of a fact by a party in a pleading, which the party claims to be able to prove. Allegations remain assertions without proof, until they can be proved
“Good News is that we have tracked the attacker, with all the proofs.” ….
and what about the above statement …. I assume by “attacker” here you meant “mr.c0d3r” …. or no?
you should have said that “we have tracked the suspected attacker” ….. right :-)
anyway, if these are all of your proofs which you have shared with us then I am sorry it is a wrong allegation .. but at least it is a starting point, I hope you find you actual culprit :-)
I appreciate your concern, however, allow me not to prove all this here : – )
but…phir kidher?
Bhi Jan main Kuch Samja nai
wasa Bhi aap Registration On Krdo
Kafi Problem hoti ha as tra
ok ac you wish and 1 more congrates for you for why guess…..
a hacker can find valun. in site and then hacked it but at this time the hacked can’; fin any valun. so he can do a final and esay action and it can do any one include not an hacker so its means your site “SECURITY LEVEL IS HIGH”
Congratulation :)
Of course mr.c0d3r and his “Good Fellas” (as mentioned in http://imstudent.net/) are notorious but the proof you had mentioned above does not prove them guilty :-)
By the way … I am not one of his “Good Fellas” :-)
“When sought, these IPs were registered in the name of an American ISP. When inquired, ISP was kind enough to give us the name of company who had been allotted these IPs.
As per American ISP, these IPs were registered in the name of a company called, ImageFi (www.imagefi.com). While IPs were mapped against the same VPS that hosted http://www.imagefi.com
American ISP also confirmed us traffic routing from above mentioned IPs to ProPakistani.PK – they assured us they will provide us logs, if asked.
WHOIS of http://www.imagefi.com revealed that [email protected] had the ownership of one of those domains.”
“And regarding the reported IPs, anyone can buy a server/vps hosting by simply putting domain name as “www.imagefi.com” and host name with same or whatsoever he wants.
Like one can also buy a server with host name and domain name as google.com or propakistani.pk but that does not mean that google or propakistani are actually being hosted on that server.
For that you need to park your domains there, but you can see none of my domains are there.”
Have you ever seen a person which had done some mishap and then accept it !? and have you every seen some hacker comes and give justification ? like when a person caught that much red hand then i don’t think he will accept the charges.
Plus why he fear that much like if this is the mr.c0d3r, he had already defaced lots of sites and nobody touched him then why he fear this time ?.
About this IP connection read both post and you will get idea whats happening here.
Peace
If you check … I am the first one to say “good job” in reply to this post … but only after reading the reply from mr.c0d3r, I realize that there is always two sides of coin :-) so I search myself and (may be I have limited knowledge) could not find any connection b/w imagefi and other three IPs (which you claim are the source of attackers).
You claim in this post that all three IPs belong to one ISP in USA but http://ws.arin.net/whois/ is telling a different story
I am not saying the mr.c0d3r is innocent. He and his friends might be behind all this but I guess you have jumped to the conclusion too soon (with very limited proofs)
Shahzad bahi – ips that attacked ProPakistani belongs to a company called imagefi.com
ISPs provide complete information, including credit card, name, billing dates and other info to law enforcement agencies. So, if mr.c0d3r didn’t do this – it will be proven, let’s not worry about him.
If you translate those words in urdu may be then you will understand the statement. see the reports above then see what he said here then make simple connection.
OK you want to do search then start with those attacking ips what will be your next step come up with some good case study at least Propakistani team had provided everything here so start investigation.
Let me clear you here the IP address which was used as they had showed here is a vps (virtual private server)and if you buy one you have to provide lots of info and not all the information comes out when you perform whois query. No company can share full info without any serious issue like this one. I had the same problem some time ago and when i tried to get information from service provider they asked me authenticity that i am the owner of a site where attacker had attempt attack.
So as above report shows that VPS provide gave them info that those vps was bought by mr.c0d3r and the info he shared with that company that time gets you to the domain name which is “http://www.imagefi.com/”.
This is what understand here with all those information above and previous experience.
If you are the filling the case against someone you only have to give some minor proof you don’t give all of them at same time may be they hadn’t shared everything to public.
hope i got it right and explained it well.
Peace
about this so-called “mr.c0d3r” he has been injecting into Mysql’s of many poor Pakistani Webmasters.
He did hacked many IPB forums hosted on insecure Linux Severs with some Unsecure functions opened.
In short he has caused Loss to many Online Websites.
Best Revenge should be, he should be caught, and Slapped with Heavy Fines, so he fears before doing it again.
Welldone. Whoever the attacker, should be exposed. And Best of luck ProPaki.
Aatta,
You went so fast :( …
I hope, you have good experience now to deal with such matters :)
Peace.
Very well done. I hope that the WP releases the patch for the bug soon. It would be great if you please share the remedy you implemented, so that other bloggers could secure their sites before the patch.
regards
Ghazala from TPS
Ghazal it wasn’t easy for us to avoid this attack, bug is not new it was circulating underground from November may be they got there hands on 18 and feeling exited they lunched it without thinking.
Remedy took us 48Hrs of hard work from tweaking WordPress code to server administration skills and database kungfu. Feel free to ask anything will be delighted to give some advise professionally.
my cousin’s site was also hacked last week by Real Cod3r and Shamoon we managed to track his IP, the hacker made a rar file containing whole site back-up.Aamir are u taking any legal action against the hacker?
We are planning the execution as of now
Excellent Work Guys! Impressive report!
Its really fantastic to know that you found out atlast that there is only 1 mr c0d3r on the internet (in the world)! lol . . .
Actually this was the thing which consume most of our time. We thought that may be there are sharing same name this is all but when we dig more and get deeper results where authentic.
Nice googling but having my share of experience in this field, I would say the evidence in insufficient for proving someone guilty, here is what the article tries to prove.
1) mr.c0d3r is a bad guy.. he defaces websites and may or may not be a part of pakbugz crew.
2) The domains registered for imagefi.com is under the name of mr.c0d3r.
————————————–
3) The attack originated from some IP pool which was allocated to some company called imagefi.
————————————–
There seems some problem at this point. Any one can register an account giving imagefi as a company name. as you can see imagefi IS NOT HOSTED on the IP’s you provided, (don’t know if it was previously) You can’t accuse some one just because of his past records (although there is high probability.. :P). It is a different case if you have got all the information from the VPS provider about the member registered against the ip host; including complete co-relation of the financial records aka (credit card info) if that matches you have a strong case if not.. more investigation and proof is required. I wont go to this extant of accusing some one… That is just my openion
You are simply dragging the attention other way, despite the fact you accepted it yourself that probability is pretty high that mr coder did all this.
Besides, I don’t know any other group in Pakistan doing such dirty work. downing propakistani could give them all time high recognition.
mr coder himself accepted the ownership of above mentioned domains, meaning that he is no more a hidden person, he himself revealed all the truth to the world.
Even if they didn’t attack propakistani, just in case, he is highly wanted by FIA. So whatever the case is he should be punished for his evil work.
Some may say that he did all this for fun, but what if he start exploiting your stock exchange data, other sensitive data? Will it be fun even then? Let’s stop them before they are unstop able.
meray bholay bhai waseem ….. ap bohat juldi her cheez ko such maan letay ho …. yahan koi bhee aa ker kisi ke naam se kuch bhee post ker de to ap yakeen ker letay ho ke woah usi real banday na lika ho ga … agher ap inhi cheezaon ko prove bana ker kisi ko guilty sabet kerna chahtay ho to phir I think propakistani team has very solid proofs :-)
wese mr.c0d3r jo bhee hai … bara hi na samujh hai .. aik to woah her jagha same naam use ker raha hai … 2nd apna pura biodata , home address etc. us ne net per rakha hai …. aur hamari FIA itni nikami hai ke is ke bawajood un ko woah nahi mil raha …. :-)
Sam nice point, same question was asked by other readers. let me put this more clearly here by giving some examples,
you bought 2 cars. and for registration of both the cars you have provided your mobile num home address or anything that link back to you. if somethings goes wrong, that is some accident, and you leave that car. when police or any person try to trace what had happened he will start trace from what you have left.
In this web attack case he left IPS from where attack was launched.
When we tried to trace him we asked service provider that what was the registration details and then they gave us this domain name and other info which we cannot disclose here. then we tried our best to trace his and this is what the results are.
Hope this will clear your mind and others
if he was part of the crew, most hackers groups dnt attach any site without prior warning
we shud take action against that chap…..
shud be arrested………
There are many groups that does all this in pk. but its just the better ones are always
not publicly known just because they are better at hiding themselves its always the script kiddies that get caught.
We are in an industry where anonymity is fame… I am no lawyer to any one here but in my opinion the information provided (technically .. at least publicly) does not stand a case if he has a good lawyer.
But on the other hand in PK you can be proved guilty for hacking even if you don’t know how to operate a computer … :P.
I strongly agree on the fact that even if he has not attacked this forum he has defaced other websites shown in the snapshot of report, the evil doer should be prosecuted period..
The work done is surely appreciated and is a very good initiative. It provides motivation for others to conduct similar research and make it public to increase awareness.
what a script kiddie :) rofl ….nice nice if you get to know this guy why not tell FIA about it he was involved with rehman maliks website u know
Bohat ghalt baat…pakar kar to acha kaam kiya magar hamein aise logon ki Qadar karni chahiye k wo kitne zabardast mind k person hein…i love peoples like that …coz they have outclass mind.. i Love u C0d3r
meri taraf se bohat zabardast kiss c0d3r k liye Q K aise logon ki me bohat Qadar karta hoon …
u have outclass mind brother
Amir bhai,
Few questions in my mind:-
1-do you have any timeline being given to you by FIA for that investigation and appropriate action?
2-Will you share / post publically what FIA guys share with you? / will you share FIA investigation report with us?
Great work, hope your get positive and quick response from cybercrimes division.
lolz its sounds funny……that a hacker starts doing DOS with a vps behind its personal information :D well i think you must ask some CISP Expert to check or let the NR3C decide
WTF Where my comments Goes:-s
yar this is so nice. every world know Pakistani has great talent but not great facilities. well done job Pakistan Zindabad
good work guyz…keep iy up.
Pakistan Zindabad!!
ProPakiz.. Paendabad!!
So this MR Coder is american,pakistani or indian…?
job done by you guys is excellent…!
long live pakistan…!
good work ,
Pakistanis rock.
Nice and very professional tracking approach!
I hope such people get punishment from law so that bad people stay away from damaging others on the internet.
There are many innocents using internet who are unaware of what is going on with them, but such hackers are exploiting their resources to gain personal benefit.
AOA,
Yap Hacking Is Crime…!
Few Days Ago My Site Name “HumYouth.Com” Was Hacked By Some Iraqi Hackers Group Named Baghdadi. They didn’t damage our site too much But They Access In Admin Account..
They Hacked 22 Sites In 2 months…. wwowo
But The Good Thing Is That Our Security And Scripting Is Good To Defend…!
& After Our Tracking We Found There Is A Relation between PKBUGS[dot]com and that hacking Group.
We Are Going To Report To The Police And FIA about relationship between Hacker and that criminal site owners & wait to see wht nxt happened
AOA,
No doubt hacking is crime. Pro Pakistani has honest employees. All cradit goes to HR Department
Long Live Pakistan and pro Pakistani.!!!!
i m cod3r:) haha :D
Inbreeders can only hack and do destruction. Hope Government will put tax on making new children in Pakistan.
This was a childish attempt to bring down a great resourceful website. PKForums guys must be jealous.
rape that nigger!
Good work propakistani.. you guys are genius
That’s really bad. However, I must say welcome back Propakistnai.
According to my observation, hacking is mostly done in countries where general frustration level of population is huge and poverty is wide spread.In 90s during break up of Russia, most of hackers of world were Russians.I am interested to do research on minds of people who do hacking, and I think its same way as minds of criminals works and has motivations from social injustice, revenge and angry youth.
Strangely, our enlightened and innocent people claim Pakistan has got TALENT that first virus of world was made by a teenage Pakistani. My question is if Pakistanis has got TALENT, why they could not make first computer rather than a first VIRUS. And i strongly believe Pakistanis don’t have any special Talent and I have no hope from future generations, because history tells us best lesson. Pakiz make name in destruction than construction.
i having lot of programmer frndz. according them hacking is not stoppable.
hacker do any thing. that programmer can’t do
and dear usman making virus is also a construction
(note:)don’t say paki or pakz in arbani language it’s mean SHIT
Hi guys, about hackers, I’ve a request.
There is a british girl, who hack and delete my myspace profile every time I create one. I don’t know, how to get rid of her.
Please help me out.
Hello man. u need help about myspace. i dont know much about myspace but i can help u get rid of her.
just pm me here
[email protected]
by the way ….good work pro Pakistanisssss
and my request is form propakitani to give respect to these hackers because after all they are at least well educated in programming and ip networks… so u or any other good organization should give them good job so that they can contribute there part in the progress of network and database security in pakistan.
Good Job
Pro Pakistani Ur Managment is also a pure Pakistani
from
http://www.karachiwalo.tk
Assalam O ALaikum
Sab se phelay to COngrates TO Back Again PROPAKiSTANI
and this is very badly for mr.coder he called him self pakistani hacker so sharam ani chayey mr/coder ko apany hi mulk ki site ko Nuqsan Pohancah rahay hai Shame on all those hacker who defeace our country site :/
and Admin App logo nay koi action liya ya nahi against mr.coder and you was say tha “we have All information about his” include contact number and address so app log osay arrest kyun nahi karwatay.
And 1 more thing app logo nay FIA Cyber crime cell main report ki to hai but app ko yaad ho na chayey kay jo LOg ( FIA ) apni website karnay walo ko trace nahi karsakay woh app logo ki kya madad karay gay so take action youself this is my advice what about you admin and All you dept.? pla reply
Wel… first of all i have heard that mr.coder denied that he hasnt done the attacks he accepts that his i.p and domain and was used but if u r a computer much litrate then u know very well to know how to use sum ones i.p or domain for attack…
and if chalein 2 min kay liye maaan bhi lain ka propakistani web kay admins bhoat genius hain or they ahve stopped teh attacks then why website 4 days tak band rahi ? 18th ko attacks hoye and 22.d ko web wapas working condition main aye lolz i m amazed those pplz who said ka well done and this and that ary bhai agar attacks save kiye hoty tu web 4 din nahi maximum 4 ghnaty main working condition main hoti …
jisay jo kerna tha wo ker gaya and u have lose it.. just accpet the truth …
or 1 more thing Mr.C0der ek pakistani hai agar wo itna capable hai bhi tu wo attacks kahan per attack karegaa apny hi mulk ki webs ko target karega? matlab mind tu use ker hi nahi rahe na yaar …
her hacker ka ek aim hota hai … uska aim pata bhi hai apko?
hackers has its own mentilaty…
ye bewaqufana discons kernay say bhatar hai ka kuch or kam kerlo bhai … maan liya bhai tum bhoat baree genius ho propak admins but mujhe tu is baat pay hansi arahi hai ka ye log jo comments day rahe hain ye khud kitna janty hain is field kay bare main or agar janty hain tu inhay ye nahi pata ka 4 din tak web band rahi….!
well whatever …!
I am having a big network of sites and I haved faced the same situation as aamir. I Contacted NR3C with all the docs and now I got the letter of the case register and they are doing the action/arrests/raid.
I can share the letter confirming the action and raids.
Nice job
very well job by propakistani team.
Good Job
duhh! If you guys were on linux; all you needed to do was to implement connection rate limit; can be done with 1 line of an iptable command…
just an FYI if you face this in future…
Great Work friends, Now you can open private detective Agency :) & help us to find out the reality of Abbotabad Drama.
lol u still cant trace him noobs :D
https://uploads.disquscdn.com/images/ebe3809688a0d5db0443821ed6a082f15662717bf2f2de72b5e0a05bcf952f59.jpg
i like it