
In a blog post, cloudflare mentioned mitigating a DDoS attack, with 20Gbps twenty-four hours a day for over three weeks, and PTCL was found to be a major contributor for this DNS amplification DDoS attack.
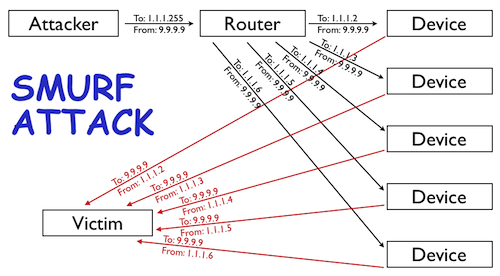
First, to understand an amplification attack, lets assume a scenario in which attacker sends ICMP requests (i.e., ping requests) to the network’s broadcast address (i.e., X.X.X.255) of a router configured to relay ICMP to all devices behind the router. This attack is called SMURF attack.
The attacker spoofs the source of the ICMP request to be the IP address of the intended victim (i.e. the target IP).
Since ICMP does not include a handshake, the destination has no way of verifying if the source IP is legitimate. The router receives the request and passes it on to all the devices that sit behind it. All those devices then respond back to the ping. The attacker is able to amplify the attack by a multiple of how ever many devices are behind the router (i.e., if you have 5 devices behind the router then the attacker is able to amplify the attack 5x, see the diagram below).
To avoid such scenarios, network operators configure their routers to not relay ICMP requests sent to a network’s broadcast address.
DNS amplification attacks are even worst, because DNS requests are transmitted over UDP, just like ICMP, but a small DNS query can generate 50X response from DNS resolvers. In other words, an attacker can achieve a 50x amplification over whatever traffic they can initiate to an open DNS resolver to the target victim IP.
Network operators running a recursive DNS resolver usually ensure that they only respond to queries from authorized IPs on their network or trusted networks only. However, that’s probably not done on PTCL routers.
PTCL routers, as claimed by cloudflare, are not configured as these DNS servers are configured to accept DNS queries on their broadcast IPs from any IP address.
Cloudflare says that it identified 68,459 unique DNS resolvers participating in the 20Gbps DDoS attack, out of which 45,595 DNS resolvers are part of PTCL network.
A network engineer working in local ISP, who wanted to remain unnamed, agreed to cloudflare’s claims and said that DSL routers are usually the real culprits. He said that DSL routers amplify such kinds of attacks, which are misconfigured or re-configured by the customers.
Cloudflare said that they can assist operators (such as PTCL) in identifying the IPs of all open DNS resolvers in getting them correctly configured. Cloudflare has welcomed the operators to work along to clean up their networks.

























Nice!
What Security experts are doing there :)
Playing games. Watching porno.
Nice
Why dont the people at PTCL fix this? Amir you can write to PTCK and let them know.
Azeem
http://ibmuet.wordpress.com/
So this explains why I have to enter those cloudflare captchas all the time :(
Yes, exactly. This is why we can’t use cloudflare – because cloudflare will regard majority of traffic coming from PTCL as spam
Oh My Gosh…..
Deploying a 20+ Gbps DDos Attack,Must Be 60000+ Net Of Bots…..
Well Bros…
No once Can Do Significant Measure,
When We Do a Valid URL Request(Like We Google ),It Send a Request to Server to Send required data to the Requested PC.
DoS Attack Act in Same Way,So its Quite hard for the server To Understand Which Request is valid and which one is A Bot Attack……..
In that Cases Networks Apply Takes Counter measure like CAPTCHA,But it will Bring all Trouble to user ,who will have to enter A captcha Each time he Even Opens Google….
Please reread..
the problem is not that DNS router is replying you.. the problem is that your request to DNS Router has prompted the network behind / linked to the router pinging you..
Today’s even tiny firewall disable that IP address within a sec..
but this condition gets really entertaining if we include Zombie Computers into scenario.. :-)
What should end users do? We know our ISPs are incompetent retards. They are not going to do anything.
Any Update.