The emergence of social media networks has made it easier for us to be connected with others. Unfortunately it brings with it many security and privacy related issues.
Social networks are increasingly being used as a tool for identity theft, stalking, harassment, invasion of privacy, and other forms of violence.
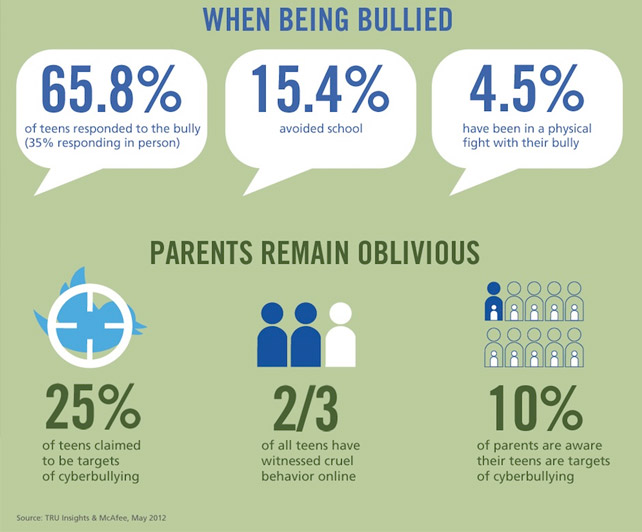
 Cyber Bullying
Cyber Bullying
The definition of cyber bullying is bullying which takes place using electronic technology. It encompasses equipment such as cell phones, computers, and tablets as well as communication tools including social media sites, text messages, chat, and websites.
Online violence, including bullying and harassment, can be severely traumatizing and humiliating for the victims and their families, with sometimes serious consequences. Therefore it is important for everyone to be aware of preventive as well as remedial measures for protection online
Protecting Yourself Online
This section aims to provide tips on maintaining digital security and privacy, as these are considered essential in helping with online safety. Following these practices can help prevent violations of privacy, blackmail, harassment and bullying etc.
Password Security
Lock your screens when away and restrict information shown by notifications. Don’t leave your phone unattended!
- Don’t use simple passwords like dates of birth, names of your loved ones, words in a dictionary etc., as these are easily hacked by those intent on theft, stalking etc.
- Don’t use the same passwords everywhere. Use a good browser extension like LastPass to manage your passwords if you have trouble remembering them.
Social Media Security
- Do not share your private plans on social networks as it makes it easy for stalkers to track you down.
- Cyber stalkers usually tend to be people you know or have interacted with. A useful practice against hacking is to use a separate email account for social media accounts and to keep it confidential. This should make hacking into your other accounts harder.
General Internet Security Advice
Use two-step verification and secure all your accounts. The two-step verification system is available for Google, Twitter, Facebook and Outlook email accounts.
- Sometimes it helps to search for your name on the Internet to find out if there is any information on you on the Internet. If you find your pictures or personal information on websites you have not authorized, you can request the webmaster or the service provider to remove them.
- Inform your family if you are facing any problems. It is important to keep them in the loop lest there are any issues later.
- One way to avoid cyber-stalkers is to use applications such as True Caller (available for Android and iOS). Such applications crowd source user information from the phones of other users and can help identify unknown numbers.
- Do not feed the troll/bully. Ignoring and blocking are frequently successful, especially at the early stages of harassment.
Underage Users
Extra care must be exercised for the protection of underage users of social media. They can easily endanger themselves and their families, and must be supervised in their use of social media. Minors are often targeted by pedophiles.
- Remain aware that Facebook has a minimum age limit of 13 for its users. Parental guidance and supervision is key in keeping children safe in their use of social media.
- Supervise online activity of minors as predators/pedophiles use the Internet and social media to target them.
- Educate children under your care on the risks or dangers inherent to the use of the Internet. Make sure they do not provide any personal information such as real names, addresses, their school name or phone numbers to strangers.
Deleting your digital footprint

One way to delete traces of your Internet presence is to go to JustDeleteMe. This is a directory of direct links to various websites so that you can delete your accounts.
The links are color-coded to indicate the difficulty level of account deletion. They are categorized as easy, medium, hard and impossible. Some of the links give information on how one can delete an account while there is no information for some websites.

 Lock your screens when away and restrict information shown by notifications. Don’t leave your phone unattended!
Lock your screens when away and restrict information shown by notifications. Don’t leave your phone unattended! Use two-step verification and secure all your accounts. The two-step verification system is available for Google, Twitter, Facebook and Outlook email accounts.
Use two-step verification and secure all your accounts. The two-step verification system is available for Google, Twitter, Facebook and Outlook email accounts.
























This is no way closer to the so-called “Essential Guide”. These are common sense stuff, and these days online registration form make sure all the above controls are put into place, automatically.
agreed, there is no CONFIRM security when we are online. we have to think about it America spying on various countries and they can’t stop them even after exposed, how we can?
How can we what? Do you not know that even Pakistani intelligence agencies spy on our internet traffic? Man you do not pay US taxes, you pay Pakistani taxes and this is how your own government treats you.
oh dear, what I wrote here? I mentioned NOBODY IS SAFE when going ONLINE…
just given an example the LEVEL OF SPYING to give understanding, we all knew about it if our government has cyber laws implemented then they are watching out network traffic.
There is zer0 chance that CIA or NSA will come after me. I am just a nobody. Unfortunately given news reports, not the same with local law enforcement. There ==ARE== captured people who are criminals who work locally.
ha ha ha… here are various claiming the same as you but who knows we all are victims too. anyway, if we are not involve in any criminal activity this is the only way they will not after us, but they are trying to spying on all of us. they means ALL from here or from abroad.
So what? Their spying is practically background “noise”
But not spying on me by local agencies. Tell me truthfully: if your neighbourhood thana sent a policeman to follow you all day long, how would you feel? Knowing the level of professional ethics of local government people, I think you would be upset very fast.
Now instead of him following you, he just looks at his computer screen and watches what sites you visit, what you do at your bank account, etc etc. It is one thing for State Bank and CBR to see your bank details, it is another for someone at intelligence agency who may or may not steal from you. How many dacoits turn out to be employees of the govenrment as guards or policemen?
So it is ==TOTALLY== not the same for NSA to spy on you and for local agencies.
if agencies want to FIND WHO IS CRIMINAL or involved in any means, they have to watch all type of internet connections & traffic for all types of citizens, no matter you or me… that’s why I said ” we all are victims “
Before clicking the link, I was wondering that it will be a very comprehensive guide or any ebook to download so i may arrange a cup of coffee for me but only disappointment here….. But still You discussed the good points
umm, yeah it’s essential, kinda but this could be more, i expected more
Kindly publish this in URDU language as many people who fails to take such measures are majority urdu readers.