Details
As you may know, on January 18th, 2009 at 11:15 PM, ProPakistani website stopped responding web requests. Most of the visitors were given a 500 html error – also database connection error.
We were able to bring back a optimized form of ProPakistani pretty soon, however ProPakistani server remained critical for next 48 hours – During which, we remained down for some time for maintenance.
We thank our visitors, who remained intact with us during all this and showed their tremendous concern though emails, phone calls, Facebook queries and so on.
We had promised our readers that we will public everything regarding the down time, cause for the problem and other relating information.
ProPakistani faced Hacking Attempt
The news is that ProPakistani had an unsuccessful hacking attempt, and attacker remained un-successful in defacing ProPakistani. However, he managed to do a DOS attack.
Good News: We Have traced the Hacker
Good News is that we have tracked the attacker, with all the proofs. Its first time in history of Pakistan that a hacker had been traced with all the forensic procedures being followed, systematically.
Security Operations were lead by renowned Muhammad Ali Raza. We thank Sohaib Ather for his extra ordinary services for Database and Server Optimization during this.
Below are complete details for your information only.
What had happened?
Immediately, after the attack was launched at 11:15, we thought it was a usual SQL server crash; however, server reboot and Dabatase repair and optimization didn’t work and crashed again very soon.
Database tables kept crashing, despite re-boots and repairs, even backup got crashed when restored. With-in first 30 minutes we had known that this is not software or database glitch, and it was some external attack.
ProPakistani servers are DDoS proof, so there were little chances that someone was launching a DDoS attack. After diagnosis, we were able to determine that was a DOS attack, instead of DDoS attack.
It happened due to a WordPress Bug!
We identified that WordPress version 2.9.1 is vulnerable from DOS attack. Bug lays in its coding that uses cache stressing with random parameter on multiple requests. WordPress has been notified about the issue; however, bug is still pending resolution. But we have secured ourselves, thanks to alternate technologies.
How Attacker Impacted?
The web requests (from attacker) were not coming from multiple hosts rather it were coming from a single host with random parameter on multiple web requests (dozens of them per second). These requests were of bad or long SQL requests, ending up with a database crash.
As the bug was in its core of WordPress so we couldn’t pull WordPress down. We had to come up with different solution. We tried moving the entire server to a new place, did tons of Database optimization, server optimization and all other options that we could avail.
While Shoaib Ather and his team were busy with database and server optimization, Ali Raza remained busy with tracing the route of attacker. He was able to trace back to the attacker successfully. However, information that we got was pretty shocking for us.
On 20th January, 2009 ProPakistani was working back with normal broadcast.
Who was Attacker?
Note: We didn’t penetrate into any personal computer/system, and used all publically available information for tracking.
We only had source IP at that time (through our Apache Error Logs).
Source IPs of attacker included:
When sought, these IPs were registered in the name of an American ISP. When inquired, ISP was kind enough to give us the name of company who had been allotted these IPs.
As per American ISP, these IPs were registered in the name of a company called, ImageFi (www.imagefi.com). While IPs were mapped against the same VPS that hosted www.imagefi.com
American ISP also confirmed us traffic routing from above mentioned IPs to ProPakistani.PK – they assured us they will provide us logs, if asked.
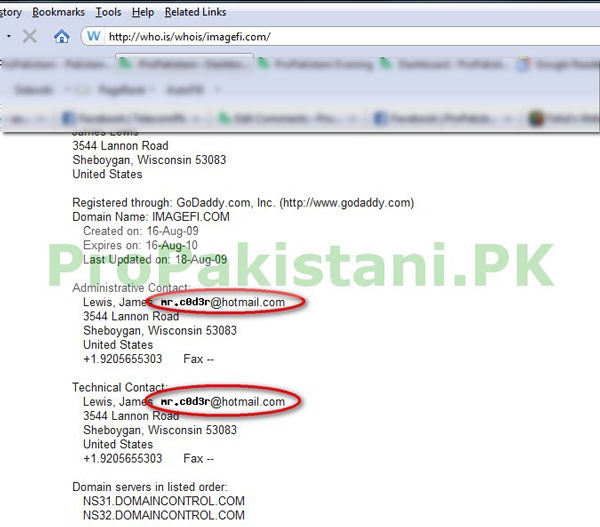
WHOIS of www.imagefi.com revealed that mr.c0d3r@hotmail.com had the ownership of one of those domains.
It was further shocking for us when we found out other websites that are hosted on same VPS, check below screen shot for proof…!
When searched on Google, Mr.c0d3r was found as a crew member of pakbugs.com. However, reportedly, he is no more associated with Pakbugs.
Digging further into Google, we disproved more interesting facts about this mr.c0d3r. He is running a torrent portal and trace leads us to India.
Googling this email mr.c0d3r@hotmail.com revealed tons of other information and soon we were able to find out that this guy is not from India.
When you Google with this particular query “mr.c0d3r country:PK” its shows that he has involvement with a local blog and forum.
So this mr.c0d3r is the guy who owns PKforums and PkReaders.com
We already have notified NR3C, with all the proofs and details to do the prosecution.
We do have all server logs saved. We do have phone numbers and address details of this person too. Will be given to concerned authorities during investigation.
This case study has been prepared by ProPakistani team.
Special thanks to Fahad Aziz and Sohail Abid for their support