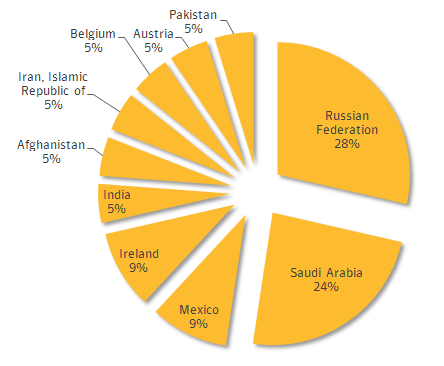
Symantec has discovered Regin, a highly advanced piece of malware that has been used for mass surveillance on governments, infrastructure operators, businesses and individuals for more than 6 years. At the moment, ten countries have been identified in which Regin operates. One of the countries is Pakistan.
The security firm said that the technical ability in the design of the bug has rarely been seen before and it equated the complexity of Regin to Stuxnet. The bug was built for long term intelligence gathering and uses some of the most advanced techniques known to spy and conceal itself.
The complexity, skills and level of resources required to create Regin can only mean that it is one of the main tools used to spy by a major nation
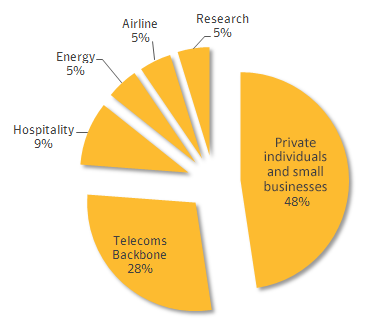
The timeline of Regin suggests that it started spying in 2008 and continued till 2011. After that, it disappeared until a new version came up in 2013. About 50% of the infections targeted small business and individuals while attacks on telecom operators were designed to get access to the calls being routed through their systems.
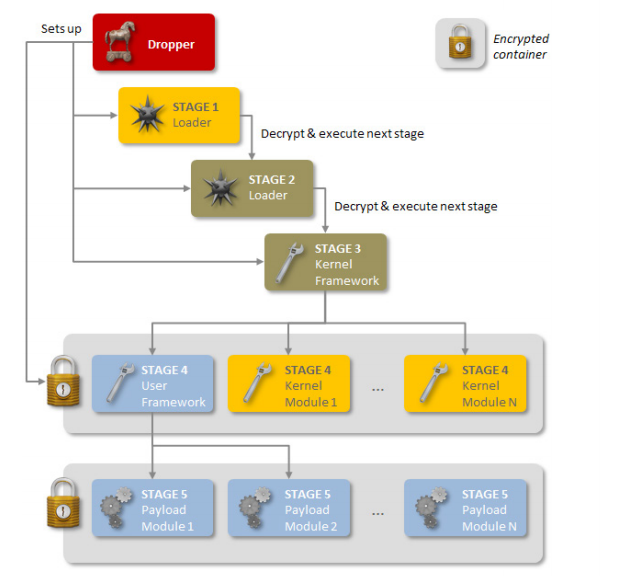
Regin is a highly versatile bug and it can customize itself according to its target. It has dozen of payloads and once installed, it can do everything from taking screenshots, steal private information, monitor traffic as well as recover deleted files. The flexible nature and advanced knowledge of some fields required to create the payloads is further evidence of the resources put into Regin.
The worrying thing is that Symantec has not been able to determine how Regin infects computers. Furthermore, even when it has been detected, it is difficult to find out what it is actually doing. In many cases, Symantec wasn’t even able to retrieve the files containing the stolen data. That is because Regin uses advanced techniques to avoid detection.
We don’t know the full capabilities, method of infection or how to determine what Regin is doing once it is detected
Those include a custom built virtual file system (EVFS) and a variant of an uncommon type of encryption called RC5. To communicate with the attackers, it uses a variety of means that range from pings, embedded commands in HTTP cookies and custom TCP and UDP protocols. What this all means is that Regin could be spying for years and go undetected.
Overall, the discovery of Regin is groundbreaking. It has gone undetected for years and everyone from powerful individuals to governments and corporations have been targeted. We still don’t know the full extent of what it can do or even how to get rid of it. But now that Symantec has gone public with the discovery, we can only hope researchers and other security firms are able to find out more.
If you want to read the white paper that details the analysis of Regin, you can see it here.


























nobody but NSA
Windows? Yawn.
Alternative? meow.
ubuntu or linux mint
no matter what you do, you will never be safer while connected to internet. Black hats are always on upper hand then white hats. Antiviruses etc are just capable of saving you from newbie hackers. they have found a new type of encryption called RC5. lol at the encryption companies which are still using the so called AES or RSA etc. if someone can create RC5 then they surely can crack your AES or RSA. and to the people who keep thinking that why the hell do they do these type of things like hacking into others lives and fetching private data or spying, trust me its the most amazing thing to do when u know how to do it properly. lol and we Pakis are just into P*rn :P
RC5 is older than AES. RSA is not the same kind of encryption as AES or RC5. It makes no sense to even mention them in the same sentence.
Get an education.
you will never become safe if you keep your self disconnected from internet, NSA has bugged several computers with a chip that can establish satellite contact with NSA server in order to transfer the intelligence data gathered from victim computers, the best way to keep safe is produce in house computers and develop your own software, microsoft has many backdoors in their windows os
What do you mean by bug? It seems to be deliberate effort which doesn’t qualify this malware as bug.
Blackhat hackers are paid more to do such stuff
.result is horrible… it seems like symentic is 5 years behind these hackers….there would be many others under the hood
Interesting story!
p.s. but I can’t see credit links for images you used from Symantec Whitepaper