With security systems getting better every year, hackers have also upped their game substantially, carrying out more attacks last year than ever before.
In 2017, cyber attacks increasingly targeted the average user as well as large corporations leading to significant financial and data breaches. If the underlying trend is any indication, we might see more hacks and data breaches in 2018, and on a much larger scale compared with last year.
A few of the most dangerous attacks carried out are listed below, along with protection measures to keep yourself safe, should you run into these problems.
1. Ransomware Attacks
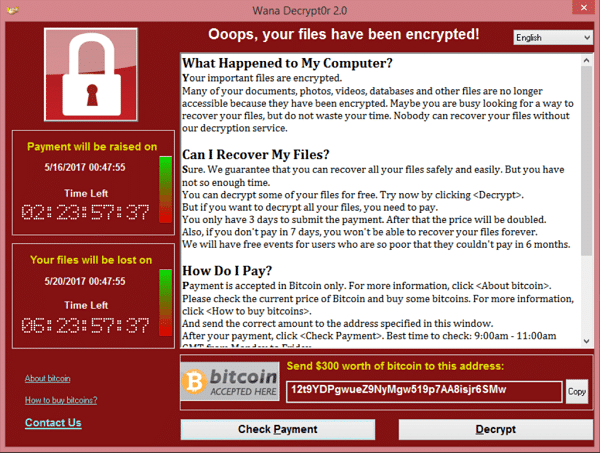
A ransomware is a piece of malware which encrypts user files and asks them for a ransom amount in return (usually as cryptocurrency) to get their precious files decrypted and usable again.
In May 2017, a ransomware named WannaCry targeted computers running outdated versions of Microsoft Windows worldwide, affecting more than 200,000 computers across 150 countries which resulted in losses of several billion dollars according to a Wikipedia article.
These stats alone show us the dangerous impact widespread ransomware can have.
How to Protect Against Ransomware
As user files are encrypted in the event of a ransomware attack, the best way to remain safe from these is to regularly backup your files to another destination, preferably on the cloud.
This way, in the event of such an attack, you can safely wipe your system and restore your data from a backup rather than paying hackers to decrypt your data. Also, you should install a good anti-virus software on your system with a firewall configured as a plus.
2. Phishing Attacks
Phishing is when a hacker appears to be a legitimate website or authority and requests vital information from the user (usually through email). Little do the users know the malicious intentions of the hacker and end up getting their data compromised.
A famous example is an attack conducted in May 2017, which affected Gmail users. According to April Glaser of Recode,
The hack was carried out by sending an email that posed as an invitation to join a Google Doc by someone in your contact list. When users clicked on the Google Doc link, they were sent to a page that actually goes to Google.com. It then requests permission for the app that the attacker wrote to access your Gmail account.
This then enabled the attacker to take full control of your account even without having your login information.
How to Protect Against Phishing
You should make sure that you are visiting the intended website and not a redirected harmful page. The most common examples of Phishing you’ll come across is in emails or on social media. You receive a legitimate-looking email or message which can deceive you into giving out your account information.
To protect yourself against these emails, you should always do the following:
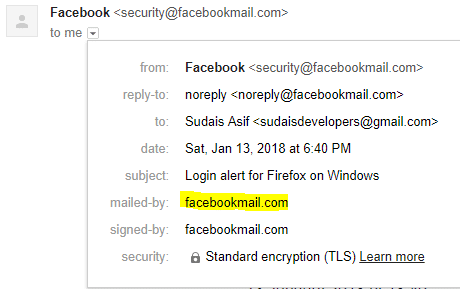
- Check the source of the email, is it a legitimate email address from the intended site? e.g. if the email is sent from Facebook, is the sender address also that of Facebook?
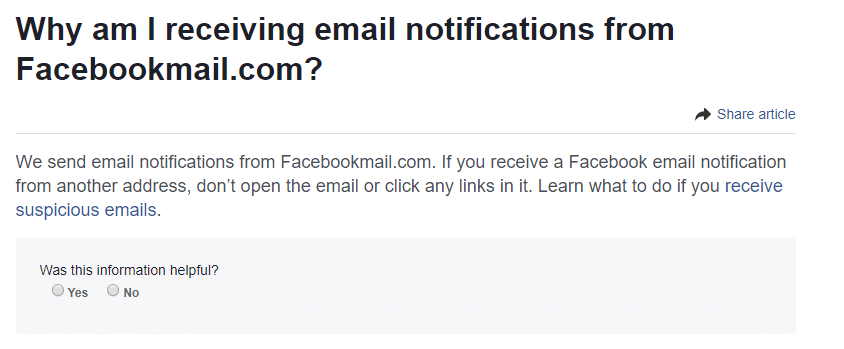
To make sure this email was from Facebook and not a hacker, I visited Facebookmail.com upon which I encountered the following URL:
with the following message:
This assured me that it was a legitimate email and not a phishing attempt.
- Is the webpage of the actual site a malicious one that looks like the actual site? e.g an attacker might be using a domain like “Facebooker.com” to impersonate the real “Facebook.com”.
- Do not enter sensitive information on pages without a valid SSL certificate.
3. Stolen Credentials
In December 2017, a company named 4iQ came across a database file on the dark web, which contained a set of 1.4 billion credentials in clear text of users of different sites including but not limited to LinkedIn, Myspace & Netflix.
This put all of the accounts at a serious risk. Just think about it, your login details could be in the hands of unknown people right now.
Not only this, your credentials could have also be stolen through ways such as password guessing attacks, the use of keyloggers which monitor your activity and social engineering attacks by guessing information needed to login such as your security questions.
How to Protect Against Attempts to Steal Credentials
- Use strong passwords with a combination of lowercase & uppercase letters, special characters & numbers along with a reasonable length, preferably above 8.
- Use 2 Factor Authentication wherever possible. As in the breach above, even if your login details were leaked, if the hackers tried to log in they would need another way for authentication for the login to be successful.
- Do not use the same password on different sites. If one set of credentials gets compromised this can lead to all your other accounts getting hacked too, so use different passwords for every site. If this seems difficult, you can use a password manager.
- Install an Anti-virus such as AVG or Avast, that can detect keyloggers or spyware.
4. New Kind of Trojan Horses – Fake Apps
Trojan Horses are known pieces of software that appear to be legitimate but in reality are malicious. If you do double click on one by mistake, you’re at its mercy as it can control your computer, delete & modify data, etc.
During the past year, as the cryptocurrency market has risen by a staggering 1200%, this has led to scammers stepping up their crypto game as well.
Many fake cryptocurrency wallet & exchange apps have popped up on App Stores particularly on the Google Play Store, which claim to be legitimate but are backed by malicious intentions such as stealing the user’s coins.
Here’s a tweet made recently by security researcher Lukas Stefanko exposing a fake wallet app.
Another famous example is that of the fake Poloniex exchange app. Two similar apps were released claiming to be official apps released by the cryptocurrency exchange, whereas in reality they were released by scammers attempting to steal user credentials.
The more popular of the apps – “POLONIEX” by a developer named “Poloniex” – managed to persist on Google Play for nearly a month, and was installed by up to 5000 users.The other one – “POLONIEX EXCHANGE” by a developer named “POLONIEX COMPANY” – reached up to 500 installs before having been removed from the store.
– Zeljka Zorz, HelpNetSecurity
As soon as the users who had installed the app tried to log in, their credentials were sent to the scammers and hence all their earnings compromised.
Here is another example of a fake app I just spotted on the Play Store. Besides these, there have also been incidents of fake apps sending SMS messages to premium rate numbers and the like.
How to Protect Against Trojans
- Always check the app developer’s information and match it with who they claim to be. The email address and developer names should match those of the company.
- Read the reviews before downloading it.
- If you’re downloading an executable file on your computer, always download it from a reputable source and scan it with a virus checker for further security.
- Not to sound like a broken record, but install an anti-virus program to protect yourself against trojans.
Apart from all of these measures, you should always keep your software up-to-date with the latest security software installed.
Corporations should also focus on increasing user awareness by conducting seminars, educating users about the latest security vulnerabilities and measures for protection.