If by any chance you are in the cyber security, then you must have overheard about this freshest and most fierce piece of computer Trojan ever developed, called CryptoLocker.
Unlike other computer malwares and Trojans which performs unusual type of activities on the victim machine, such as stealing private data, gaining access to personal information, garbling files, or to advertise political or humorous messages on the user’s screen; CryptoLocker uses entirely offbeat strategy to destroy your data and which makes your data recovery impossible.
So, what exactly is CryptoLocker and how does it works?
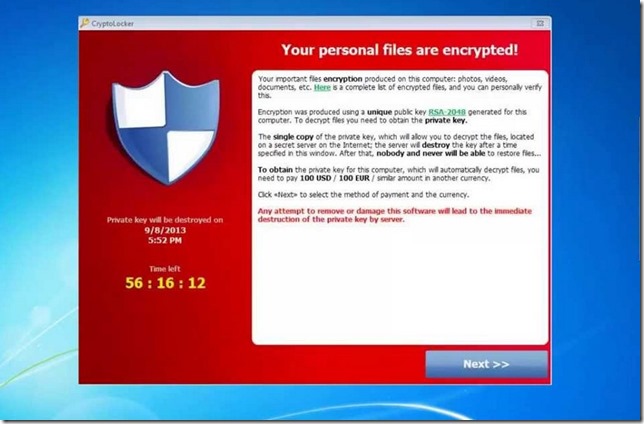
First reported in September 2013, a CryptoLocker is a ransomware trojan that expertly targets Windows based PC (including latest version of Windows 8), and annihilate stored data beyond the proficiency of any data recovery process.
In case if you don’t know, “Ransomware is a kind of malware which limits your access to your own computer, or your certain files, and asks some sort of ransom to be paid in order to unlock your PC.”
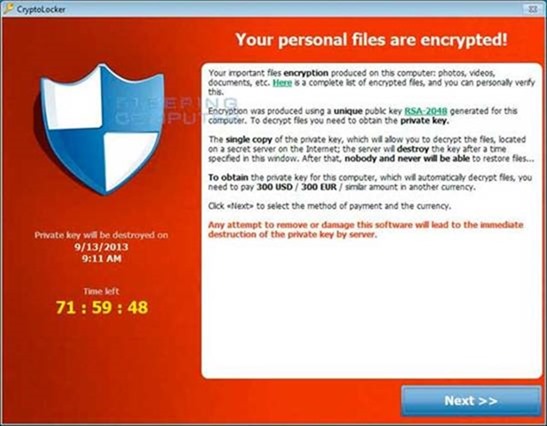
What it really does is that, it securely encrypts the data including documents, photos and videos in the victim’s machine using RSA-2048 security algorithms which is almost un-breakable.
Once the encryption is done, it uncovers itself, demanding the infected user to pay the ransom in order to gain their sensitive data back. It also forewarns the user to not try to get rid of the CryptoLocker program as it will enduringly obliterate their personal data by razing the secret-key from the server.
Considering that CryptoLocker employs RSA for data encryption, It merits mentioning here that RSA uses public-key cryptography, which means that user’s data is encrypted using the single public-key and for each unique public-key, there is a private-key; the encrypted data could only be recovered when the private-key is provided to the CryptoLocker program.
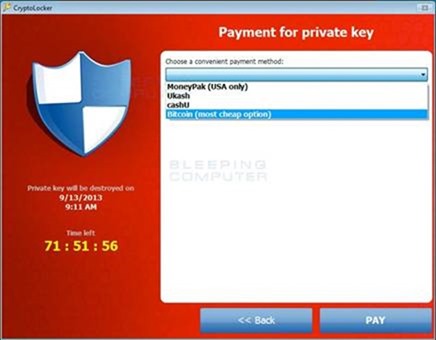
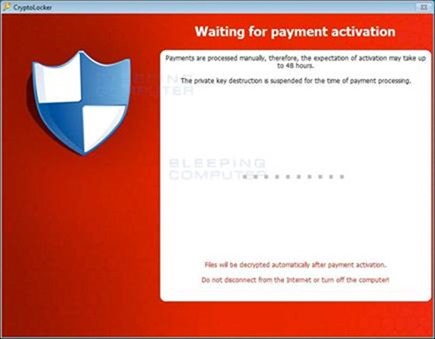
This private-key is only available on the CryptoLocker secret server on the Internet which will be provided to the sufferer if he pays the demanding amount in a given time frame, if a user fall short to pay the requested amount in the defined time, his private-key will be exterminated on the server and there will be no way left to restore his data again.
While on the other hand, paying the required fee doesn’t guarantee that your infected data will be decrypted and restored to you. So concisely, if you’re infected by CryptoLocker, you’re totally screwed.
The attacks of CryptoLocker could come from various distinct sources, including USB drives, social networks, and spam e-mails etcetera.
In one strategy, it disguises itself as a genuine email attachment that asks the user to click on a zip file. It also spreads as an e-mail attachment claiming that there had been a problem clearing a cheque, and clicking the associated link downloads a Trojan called Gameover Zeus, which in turn installs Cryptolocker onto the victim’s PC.
Ever since CryptoLocker surfaces on the Internet, there have been diverse incidents where organizations and professionals have become the prey, and have paid a ransom to revive their sensitive data.
Dell Secureworks had said that, between 200,000 to 250,000 computers had been infected by CryptoLocker so far. It is essentially well-known because of it use of robust encryption, a countdown timer and an entangled monetization scheme.
Security researchers have been digging hard to break the CryptoLocker Trojan, on the side note; one of the most efficient ways to dwindle the influence of CryptoLocker is to abstain from reading emails from an unfamiliar sender, or by creating routinely backups of your personal and sensitive data.
One other way is to keep your Antivirus up-to-date; It is always a good idea to pay few bucks to buy the premium Antivirus service, than installing the Free trial versions.






















Yet another solution: don’t use Windows. Especially pirated Windows which cannot receive updates or use Microsoft Security Essentials.
pirated OS can receive updates if you know how to:)
Linux can receive updates, too. For free. For up to five years in some cases (Ubuntu, Debian, etc, etc) And a free upgrade to the next version.
Free vs pirated: you gotta have a real need to hurt yourself to use Windows.
Or you gotta get some work done using Adobe/Autodesk software :P
I think the best solution for windows user is Bitlocker
I think we should now start moving to Ubuntu :)
I think we should stop bullshit.
Then Mac or linux.. Linux still have not some major apps, specially for graphic designers plus many tools.
Dont Use Windows…….. WTF??
Pirated Windows Can Recieve Updates. This Torjan Right Here Doesnt Gives A F_|_K If Windows Is Updated Or Not It Does What It Does!!
Microsoft Security Essentials Is The Most Crappiest AV Ever!!
So Next Time Think For A While Before You Open Your D’K Trap!!
i have been victim of this, and till date i never knew that it was trojan who blocked my access after startup(rather i have been thinking it’s Microsoft who did this after 1 and half year of updates), i simply re-install windows and use my kaspersky(commercial version provided by mine company) and got rid of that situation….my point is, if you have some registered antivirus, you get get rid of it, so easy nothing to worry about it….
re-installation is not a solution in your case u’ve lost ur data ..
Re-installing the OS to get rid from the trojan is just like killing a person when he is sick.
Simple solution to this ransomware is to “Restore your system to previous date” using “Windows System Restore”
Doesn’t work.
That will make it even worse…
Ha Ha Ha…
Funniest Computer Program Ever Seen.
Then by all means, please do infect your own PC and have unlimited laughs.
Already Have Played with it..On VMWare For your Info. :p
So you played with it in an isolated environment ?
What was the whole point of playing when it didn’t infect anything sensitive ?
Was Identifying the Server Source with HTTP and System Traffic Monitoring software
Ha. So glad I switched to OS X two years ago.
Nice to see ransom industry stepping in Computers and I.T!
Ransomware is not a new term, It is around since 1989. This was the year when first ransomware was detected, and was known as “AIDS” trojan.
Oh! Thanks. Gone through the article on wiki!
My Pleasure :)
Fortunately for me, all of my useful data is in Dropbox so I will have to spend a few hours doing a clean install at worst. I don’t even have an anti-virus installed to preserve laptop battery.. I just avoid running non-trusted executables/pirated software, disable autoplay and always inspect email attachments using Google Drive first.
This is almost exact thing i do, I do not keep any data in my Laptop at all, in fact, I keep it in an encrypted external Hard drive, and it is from where i access it, and tends to back up every single file on Google Docs right after they are produced.