First Facebook and now Samsung.
If you remember, Facebook’s sensitive information, including user data, was found on a public domain with open access recently. Turns out, Samsung may have had a similar incident.
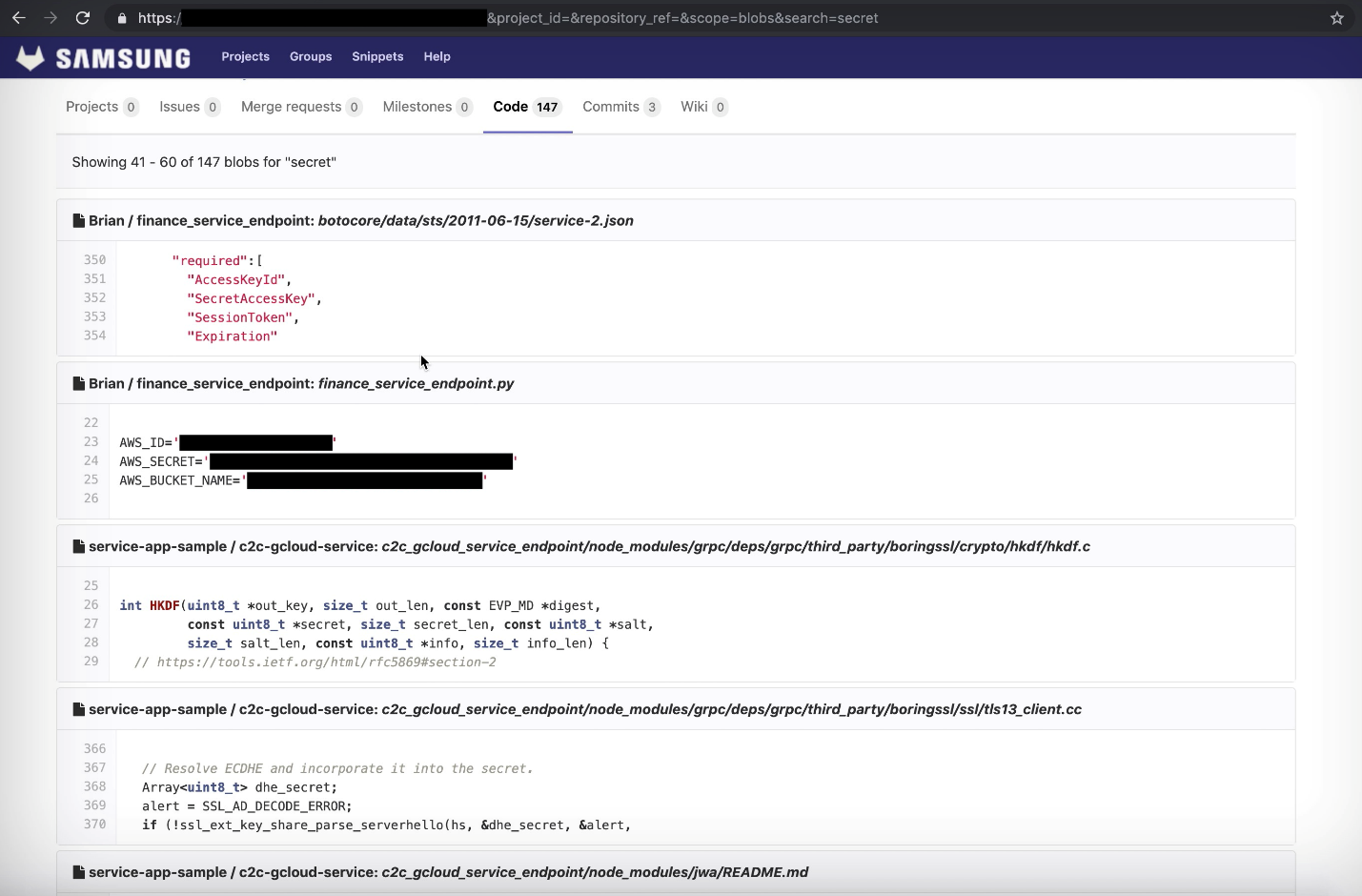
The company left source codes, Amazon web accounts and employee GitLab tokens on a GitLab instance that was hosted by Vandev Lab, a Samsung hosted domain.
The source code of projects like the SmartThings platform and Bixby services were also available on the repository. Access to all the data was set to public, and there was no password set on it and the GitLab instance was being used by Samsung staff.
White Hat Hacker
The person who discovered the publicly available data, Mossab Hussein, is a security researcher at SpiderSilk, a Dubai based cybersecurity firm. According to him, one of Samsung’s projects allowed access to an Amazon web services account which had hundreds of S3 storage caches containing logs and analytics data.
He said that many folders contained logs and analytics from SmartThings and Bixby which in turn allowed access to another 135 projects that Samsung is currently working on.
Hussein said,
I had the private token of a user who had full access to all 135 projects on that GitLab. The real threat lies in the possibility of someone acquiring this level of access to the application source code and injecting it with malicious code without the company knowing.
Hussein documented the public access given to anyone who stumbled upon the file. The following screenshot shows it in action:
Hussein is a white-hat hacker whose expertise lies in finding data breaches and privacy concerns and he is not new to reporting cybersecurity vulnerabilities. However, this was his biggest find to date. He said,
I haven’t seen a company this big handle their infrastructure using weird practices like that.
Samsung’s Response
As soon as Hussein discovered the data, he contacted Samsung, who told him the data was only for testing purposes. However, Hussein questioned the claim since the source code was similar to the published Android app for SmartThings.
The app was published on 10th April and was installed more than 100 million times, which means more than 100 million people are at risk.
Samsung claimed to have revoked the keys and passwords but they took a lot of time doing it. Hussein contacted Samsung on 10th April and Samsung revoked the keys and passwords on 30th April which is more than half a month.
Samsung has still not resolved the issue. Samsung’s spokesperson, Zach Dugan told TechCrunch,
Recently, an individual security researcher reported a vulnerability through our security rewards program regarding one of our testing platforms, We quickly revoked all keys and certificates for the reported testing platform and while we have yet to find evidence that any external access occurred, we are currently investigating this further.
Via TechCrunch