
This hacker group claims to be the watchmen of Pakistani cyber space and are believed to quietly observe things to make sure that they keep rolling smoothly.
Hacker group, having Khanisgr8 , Net_Spy , Xpired , Sho0ter and N3t.Crack3r as its members, revealed — in an email sent to ProPakistani — that hundreds of .PK domains, including google.com.pk, msn.com.pk and other country level domains for top global brands were defaced on Saturday due to security flaws of PKNIC system.
Hacker group, in an exclusive communication with ProPakistani, claimed that PKNIC servers are vulnerable to:
- Boolean-based blind sql injection
- Time-based blind sql injection
- Cross site scripting
- Sensitive directory disclosure
Hacker group provided ProPakistani with complete parameters and proofs of vulnerability, which according to experts are valid and the only reason that hundreds of .PK domains were taken down on Saturday. Security experts told ProPakistani that PKNIC is vulnerable for long and needs to be scrutinized at earliest to avoid such instances again.
ProPakistani can share the the complete details of these vulnerabilities with PKNIC if they want to resolve the flaws.
It maybe recalled that a hacker, named eBoz, had re-routed some 284 .PK domains from their legitimate servers to an hosting account allegedly owned by hacker himself, by penetrating and re-configuring the DNS and name servers of these domain names.
Following are screenshots proofs of PKNIC vulnerabilities:
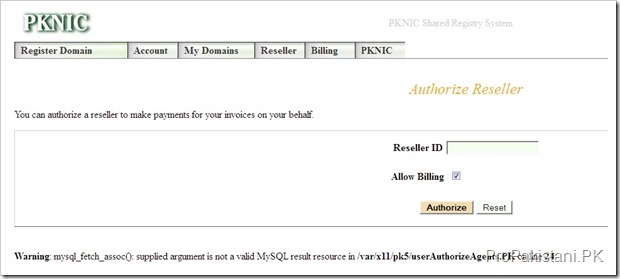
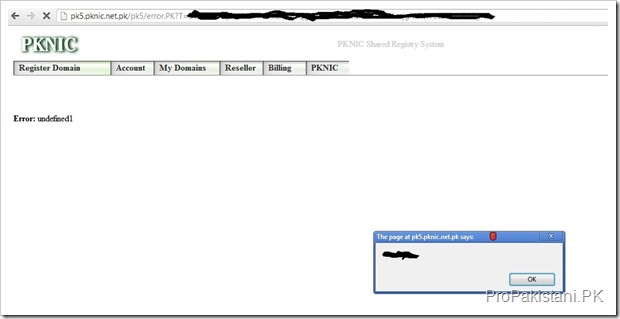





















but the real question is: if they are logged into the site (or even if they are not logged in), can they access someone else’s account with sql injection or any other attack?
Because otherwise, it’s not very interesting to find such “hacks” if you cannot get more information or access than you already had. I mean I have built websites that throw all sorts of weird errors when users input things they should not, but 0% of those inputs lead to priviliege excalation or access to someone else’s data.
Yes they can, because if this site is vulnerable to SQL injection then whole database can be accessed or manipulated. Hacker can change the preferences of any account stored in database, even if password of the account hashed. Problem exists because of the use of deprecated web technologies as i see PHP’s mysql_ library has been used in PKNIC while much improved is available since long. Only the web-developer can be held responsible in such circumstances. It is necessary to sanitize user input to make it secure, so the hacker wont be able to execute malicious script or query. If input is not filtered, then filtering the output is suggested.
They CAN, or they think they can? Again, I am being precise. Has anyone actually gained access to privileged information in another account, or modified some other account? THis is important.
I know the existence of sqli makes it LIKELY that they can but unless & until someone shows evidence that they HAVE used such an attack to change something or do something they don’t have access to, then it is all theoretic.
I know the SQL injection but i’ve done it year ago just to give a try to know how it works, at that time i found a korean anime site which was vulnerable, i wasn’t not only able to execute SQL queries but was also able to access every table in that database, interestingly developer had not hashed the password and for most of the users the password was same as it was for their email ids, even for the paypal too..that’s been my personal experience on SQL injection, it really works. Im not going to write a tutorial how i did that but if you try, search you will find many tutorials on forums, that’s what script kiddies doing. There are many software which let you know about the vulnerability of a website and can suggest you appropriate hack to apply. Personally i’ve no interest to hack people and i don’t think a person (script kiddie) as hacker who uses software developed by others to hack, till he develops something himself, and that is the only thing one can do when someone actually knows what’s being done behind the scene.
But at-least i can explain you how SQL injection works
suppose you are taking input for login and using those inputs directly in your query without filtering i.e.
SELECT * FROM users WHERE username = ‘$user’ AND password=’$password’;
it would work fine .. but from an attacking point of view the database table can be dropped by entering the following query in username filed.
x’; DROP TABLE users; —
so the executing query will be manipulated just from the inputs and it will now be
SELECT * FROM users WHERE username = ‘x’; DROP TABLE users; –‘ AND password=’$password’;
Here two queries are being executed, in second query we simply dropped the table and every thing which comes in query after “–” now will be an SQL comment. You can even insert data in table.
The simple solution of this problem will be to filter quotes from user input. That’s why sanitizing user inputs is extremely important.
Man, you are still not getting it.
I KNOW what sqli is. Read my first comment on the topic. Read what I said about how my sites react.
My question is only about PKNIC site. Has anyone SUCCESSFULLY used SQLi to take over or modify someone else’s account or data? It is one thing for Pakistani hackers to show SQLi problems with the site, but another to actually get inside and modify data.
YES OR NO. For YES, I would like to see evidence.
As it is being claimed by Propakistani, so they can provide you evidence. I explained you that if something is vulnerable to SQL injection then its possible to perform CRUD. So, if PKNIC is, then its obvious.
Sorry if i misunderstood you completely,
I’ve not tested the PKNIC as yet but from screenshots it seems XSS vulnerable.
Propakistni kasa bach gaya?
ultimate question, share something aamir bhai
ZDNet reported this too http://tinyurl.com/cbzg83p
Pakistan kay har cheez main flaws hai. itni important website and having these issues terrible.
They must redesign the code and to check every aspects with any security expert firm.
I don’t know how internic provided such license to this firm and i am dealing with this last many years and they really bus earning and earning and nothing doing for betterment.
Man you do not remember the old days of pknic where to do any domain registration, change, etc you had to fill out a text-based form and email it. The website was NOT dynamic at all. Only when they came out with .pk did they start trying dynamic. Rumour has it that they had a web form for input a decade ago but got hacked so they went static until 2006.
Interestingly pknic still does remember those text-based form domains — in fact they still have them active as “legacy” domains:
The domains registered using text domain registration form (email template) are categorized are legacy domains.
The text domain registration form is no longer used. For the near term, you can modify the legacy domains without requiring a login, using the the Authorization Codes, on this web site. However, it is required that all legacy domains be moved to an online account, in due time.
BTW: pknic is owned by one “Mr. Ashar Nisar” who has made millions from pknic (but seems not to have spent a penny on it, seeing it’s sorry state even today). Also surprising is the sorry state of enterpreneurship in Pakistan if enterpreneurs.pk had to name him entrepreneur of the month in 2011…..
(http://entrepreneurs.pk/2011/03/27/ashar-nisar-the-pk-man-entrepreneur-of-the-month/)
i hate hacker dumb as*
Bang on. Akheeer ho gaye!
Pakistani hacker group just wanted to seek attention for the jobs as there are few left lol.
my blog lost 70% daily traffic during previous one week. Can it be becuase of Google Pk hacking or some other reasons
Well I think its off topic but I wanna ask a question and I hope
someone reply that inappropriate question cauz I didn’t find any answer
from my friend yet.
Q: I am interested in VB .NET. Which is good
academy in Rwp/ISB area for it. Only I know is NICON which has just 2
month course and charging 12500 for it. I don’t care about the fee. I
just want to learn it from professional and don’t want to stick with
self study.
Sorry again for asking off topic question here.
hahahaha @mujay tu yeah smaj aaya hay k Hackers ju exclusively sub info dr rahy hain
hotspot shield http://www.hotspotshield.com/en yeah vpn use kr rahy hain hahaha