Intel and ARM processors were hit by the age-old Spectre vulnerability once again last week. Since AMD has a completely different design for chips, it was able to dodge the harm last week, but that victory was apparently short-lived.
Security researchers from Intel have now released a white paper that details how AMD’s chips are having code exposures as well. AMD was quick to introduce a solution that would otherwise take years to repair. But it did not prove to be as efficient as initially thought.
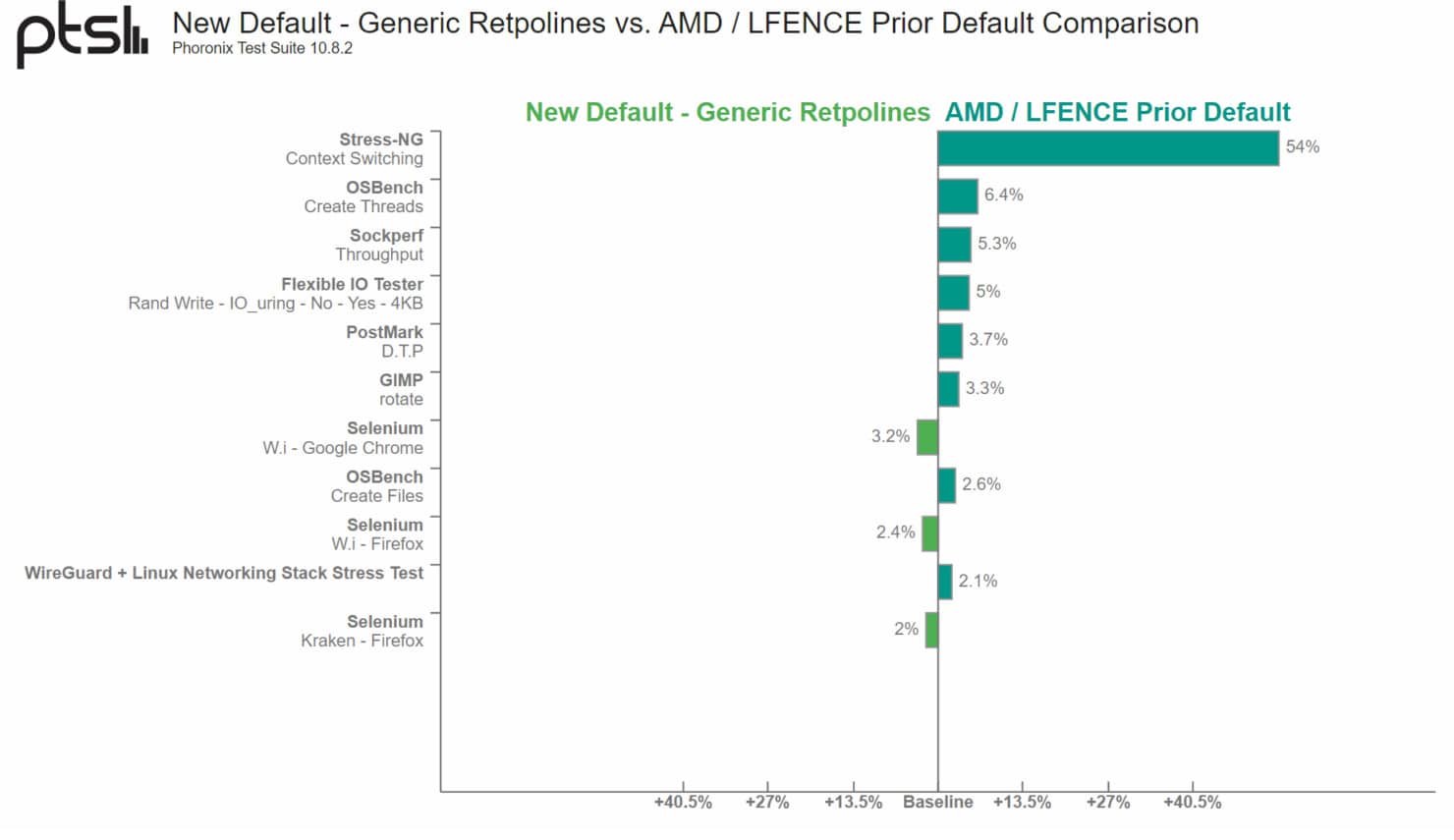
The research team pointed out how AMD’s LFENCE/JMP-founded Retpoline code to avoid Spectre attacks was inadequate. Tech blog Phoronix noted that AMD changing its Retpoline method for Spectre V2 was showing up to a 54% performance drop. The drop was observed to be higher on AMD’s Zen-based processors.
As a result, AMD is now initializing the recommended “generic” Retpoline guideline to manage the vulnerability more efficiently. This was highlighted in a new security bulletin shared by AMD that reflects the new efficiency for keeping their product safe.
AMD retpoline may be susceptible to speculation. The speculation execution window for an incorrect indirect branch prediction using LFENCE/JMP sequence may potentially be large enough to allow exploitation using Spectre V2. By default, don’t use retpoline, lfence on AMD. Instead, use the generic retpoline.
The performance difference with AMD’s new approach remains to be seen but we have high hopes since it is claimed to be more efficient with performance as well as security.